What is Security-as-a-Service?
Security-as-a-Service (SECaaS) is no longer a niche solution. It’s become the front line for how SaaS companies protect user data, maintain trust, and scale securely.
Instead of building costly, in-house security systems, companies now subscribe to cloud-based solutions that handle everything, from malware protection to compliance automation.
It’s flexible. It’s scalable. And in today’s threat landscape, it’s essential.
Table of Contents
Why Is Security-as-a-Service Gaining So Much Attention?
We’re in the middle of a cybersecurity arms race. Startups are under pressure to move fast, but also stay secure.
And here’s the reality: most SaaS companies aren’t equipped to build a fortress from scratch.
So what do they do?
They rent one.
SECaaS gives you enterprise-grade security tools, firewalls, intrusion detection, and access controls, without the enterprise-grade cost or complexity.
How Does It Work?
You pay a monthly or annual fee, and the vendor handles the rest. The architecture usually includes:
- Endpoint protection
- Identity and access management (IAM)
- Vulnerability scanning
- Email filtering
- Data loss prevention (DLP)
- Encryption services
Everything’s managed remotely, updated in real-time, and integrated into your cloud environment.
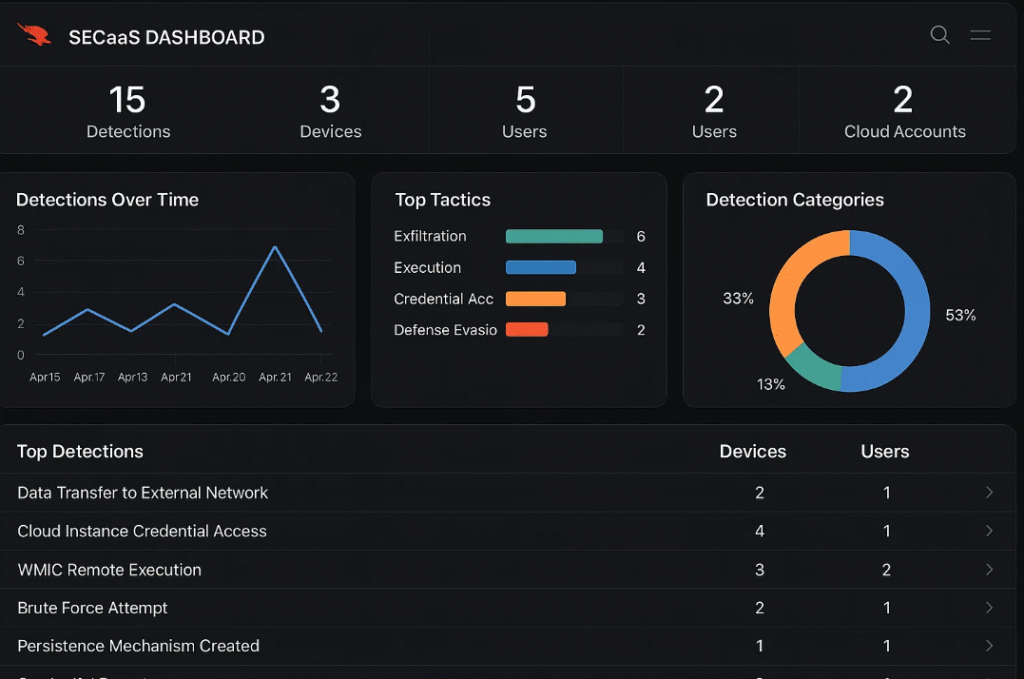
Why Should SaaS Startups Care?
Because data breaches are expensive.
Not just in dollars, but in reputation. Customers don’t forgive easily when their data is mishandled.
And when your startup lives and dies by MRR and retention, you can’t afford to get this wrong.
Security-as-a-Service doesn’t just protect your backend—it protects your brand.
Isn’t Security Just a Feature of the Product?
It used to be.
But in 2025, security is a product in itself. Buyers ask about it. Investors expect it. Regulators demand it.
If you’re in FinTech, HealthTech, or EdTech, compliance isn’t optional—it’s baked into your GTM motion.
And if you’re not showing SOC 2 or ISO 27001 readiness, you’re already behind.
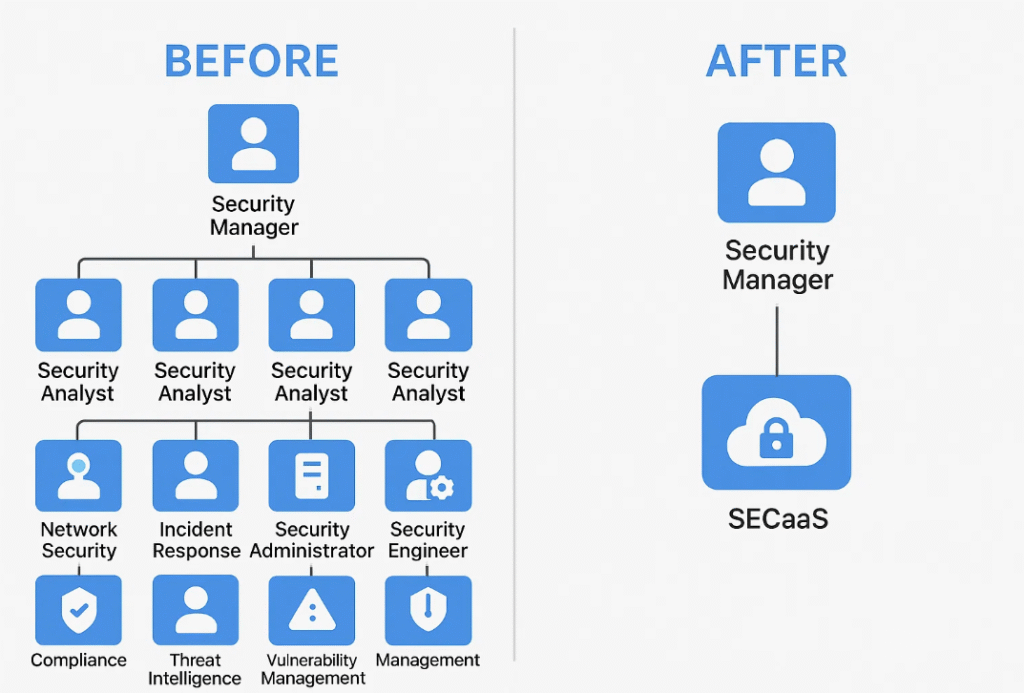
What Problem Does SECaaS Solve for Lean SaaS Teams?
Most SaaS teams don’t have a CISO.
Some don’t even have a dedicated DevSecOps hire.
Security-as-a-Service plugs that gap instantly. It acts as your outsourced security ops center—handling alerts, responding to threats, and ensuring compliance.
It gives you scale without staff.
Is Security-as-a-Service More Cost-Effective Than In-House Security?
Let’s do the math.
Hiring a security engineer? ~$130K/year
SOC 2 audit readiness? ~$25K+
Ongoing compliance + threat management? Who knows.
With SECaaS, you get the equivalent of a security team—tooling, monitoring, remediation—for a fraction of that cost.
And it’s not just cheaper. It’s faster. You don’t spend 6 months building pipelines. You get real-time protection from Day 1.
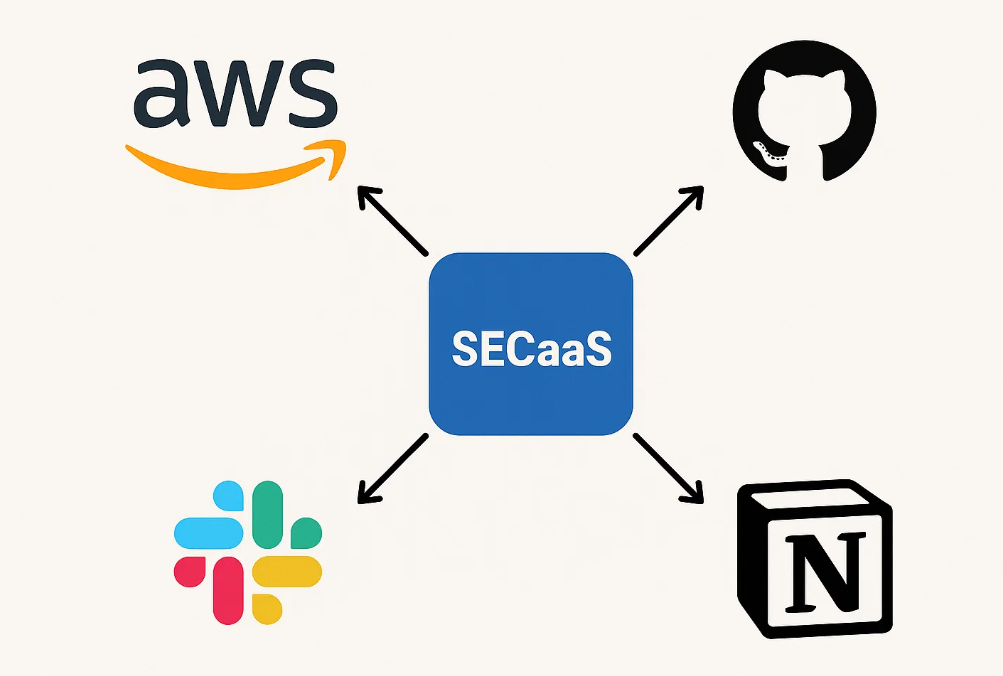
Can It Integrate With My Existing SaaS Stack?
Yes. That’s the whole point.
Modern SECaaS platforms integrate with:
- AWS, GCP, Azure
- Slack, Jira, Notion
- GitHub, GitLab, Bitbucket
- Zapier and other automation tools
APIs, webhooks, and plug-ins make it easy to tailor the solution to your workflow.
How Does It Impact Compliance (SOC 2, GDPR, HIPAA)?
This might be the most underrated benefit.
Most SECaaS tools come pre-configured with frameworks for:
- SOC 2
- ISO 27001
- GDPR
- HIPAA
- CCPA
You’ll get alerting, documentation, audit trails—all the evidence needed to pass audits or respond to data requests.
Think of it as compliance in a box.
What Happens If There’s a Breach?
Here’s where SECaaS proves its worth.
In the event of a breach:
- You get real-time alerts
- Your system auto-isolates compromised endpoints
- Logs are generated instantly for forensic review
- Some platforms even kick off incident response workflows
It’s proactive, not reactive.
You’re not scrambling. You’re executing.

What’s the Downside?
Every tool has trade-offs.
With SECaaS:
- You rely on a vendor’s uptime and policies
- There can be data residency concerns in certain countries
- You still need someone to oversee configuration and alerts
But in most cases, the benefits far outweigh the risks, especially if you choose a reputable vendor.
Who Are the Top Players in Security-as-a-Service Right Now?
Some of the top SECaaS vendors include:
- Cloudflare Zero Trust – for network and app-level security
- CrowdStrike – endpoint protection and threat intel
- Zscaler – secure access service edge (SASE) pioneer
- Tines or Drata – compliance automation
- Splunk + SOAR – enterprise-grade log monitoring
Each has different strengths depending on your stack, team size, and risk profile.
Will Investors and Customers Ask About Your Security?
Yes. Constantly.
Security is now part of the sales process. It’s part of due diligence. It’s a core part of your brand’s credibility.
Expect questions like:
- How do you manage user access?
- Do you encrypt data at rest and in transit?
- What happens if a developer’s laptop is compromised?
- Are you SOC 2 compliant?
With a strong SECaaS setup, you won’t just answer those questions, you’ll impress.
What’s the Future of Security-as-a-Service?
The future is automation.
AI-driven threat detection, self-healing systems, continuous compliance monitoring—these are no longer buzzwords.
Vendors are racing to build “zero click” security, where you don’t just get alerts—you get resolutions.
Expect more platforms to become no-code, API-driven, and built for non-security people.
The goal? Make security invisible, but ever-present.
Related Article: https://www.techtarget.com/searchsecurity/definition/identity-access-management-IAM-system
Should You Invest in Security-as-a-Service Right Now?
If you’re building anything SaaS, the answer is yes.
It’s no longer a “nice to have.”
It’s the foundation for your credibility, compliance, and customer trust.
And the best part? You don’t need to be a security expert. You just need the right partner.
x
Real-World Breaches: What Happens Without Security-as-a-Service?
Take the 2021 breach of CodeCov, a SaaS platform used by thousands of developers.
A simple misconfiguration in a Docker image led to months-long exposure. Attackers injected malicious code and stole credentials from customer environments, without being detected for weeks.
Now imagine that same scenario with Security-as-a-Service in place:
- Automated detection would’ve flagged the anomaly
- Secrets would be encrypted or vaulted
- Real-time logs would show timestamped access
- Alerts would reach the right person immediately
The breach wouldn’t just be detected—it would be contained.
A Simple Checklist to Evaluate a Security-as-a-Service Provider
Choosing the right provider isn’t about getting the fanciest features. It’s about matching your stack, your risk profile, and your internal resources.
Here’s what to look for:
Ease of Integration
Does the platform plug into your cloud provider, Git repos, CI/CD pipelines, and team communication tools?
Coverage
Does it offer full-stack protection—endpoint, identity, email, code, cloud?
Compliance Readiness
Does it offer automated reports or frameworks for SOC 2, ISO, and GDPR?
Threat Intelligence
Does the vendor stay updated on real-world attacks, not just theoretical risks?
Response Automation
Does the system trigger alerts or take automated actions (like isolating devices or revoking tokens)?
Transparency
Do they share their internal security practices? Are they SOC 2 certified?
Common Myths About Security-as-a-Service
“We’re too small to be a target.”
In reality, small SaaS startups are easier targets. They often lack strong defenses, and attackers know it. Some ransomware groups automate the targeting of small cloud platforms just for this reason.
“Security is the job of the cloud provider.”
AWS, GCP, and Azure operate on a shared responsibility model. They secure the infrastructure, but you secure what you build on top of it. SECaaS bridges that gap.
“It’s better to build security in-house.”
That might be true at scale. But for startups, building in-house security is like building your datacenter—it’s outdated and inefficient. Security-as-a-Service gets you operational on Day 1.
[Image Suggestion: Side-by-side myth vs. fact graphic]
A simple comparison table of myths vs reality (can be branded with #E02B20 accent).
What Metrics Should You Track Once You Deploy SECaaS?
Security isn’t just about being safe—it’s about knowing how safe you are. Metrics help.
Track these:
- MTTD (Mean Time to Detect) – how long it takes to identify a threat
- MTTR (Mean Time to Respond) – how long it takes to contain or fix it
- Coverage Score – % of assets monitored
- Policy Violations – How often users break best practices
- Audit Readiness Score – how close you are to passing a compliance framework
These metrics let you show the ROI of your SECaaS investment to your team, board, or investors.
Transitioning from DIY Security to Security-as-a-Service: A Step-by-Step Guide
Most teams don’t start with zero. They’ve got some tools in place—maybe a password vault, some AWS IAM roles, a VPN.
But it’s duct-taped together. No central view. No automation. No alerting.
Here’s how to switch over:
1. Inventory Your Current Tools
Document everything: IAM roles, cloud security settings, logging tools, endpoint tools.
2. Define Your Threat Model
Are you worried about internal access leaks? External breaches? Compliance gaps?
3. Pick a Provider Based on Needs
Some platforms specialize in compliance. Others in network security. Match the tool to your weakest link.
4. Start with Read-Only Mode
Deploy the SECaaS tool in “monitor only” mode first. Understand its findings before letting it take action.
5. Set Policies + Automations
Define alert thresholds, escalation workflows, and who gets notified when.
6. Train Your Team
Make sure everyone knows how the system works, what’s monitored, and how to respond to incidents.
7. Retire Redundant Tools
Once SECaaS is fully live, shut down overlapping tools to avoid noise and cut costs.
Why Ad Labz Recommends Early Adoption of SECaaS
We’ve worked with SaaS companies that scaled fast, but lost deals because they couldn’t answer basic security questions.
Security doesn’t just protect—it sells.
- It helps you close enterprise deals
- It keeps you compliant as you grow
- It avoids fire drills that burn developer time
If you’re investing in growth, you should also invest in protecting it.
Comparing the Top Security-as-a-Service Tools
| Platform | Strengths | Ideal For | Compliance Features | Pricing Tier |
|---|---|---|---|---|
| Cloudflare Zero Trust | Fast setup, SSO, access control | Remote teams, network protection | Supports SOC 2, ISO | Mid |
| CrowdStrike Falcon | Endpoint defense, threat detection | Device security, hybrid teams | Detailed audit trails | High |
| Zscaler | Zero Trust + SASE | Distributed teams, secure access | Enterprise-ready | High |
| Drata | Compliance automation | SOC 2/ISO readiness | Pre-built control mapping | Mid to High |
| Lacework | Cloud workload monitoring | DevOps environments | Policy & config audits | Mid |
Real Startup Use Cases
Case 1: Series A SaaS Startup
A growing SaaS CRM tool needed to secure its pipeline to close enterprise deals. Their engineering team was already stretched. They deployed Drata to automate SOC 2 compliance and used Cloudflare to lock down internal tools. Within six weeks, they passed their audit and closed their biggest B2B customer.
Case 2: DevOps-Heavy Analytics Company
They were deploying code daily and constantly opening access to staging environments. After a minor access leak incident, they added Lacework to monitor container activity. Within days, it flagged improper IAM roles that were otherwise invisible. They fixed it before a breach could occur.
Case 3: Remote-First SaaS Team
With no central office, every team member accessed sensitive customer data from their laptops. They added CrowdStrike and Zscaler. Suddenly, all traffic was encrypted and monitored. Even during a laptop theft incident, no customer data was exposed.
Security-as-a-Service isn’t just theory. It’s helping real startups tighten controls, win business, and sleep easier.
FAQs About Security-as-a-Service
Is my customer data still private if I use SECaaS?
Yes. Legitimate SECaaS vendors follow strict data handling policies. Most tools don’t store your customer data—they analyze metadata or behavior. Always review their data residency and privacy documentation.
Will SECaaS slow down my app or site?
Not if configured properly. Most services run in the background, monitoring logs, endpoints, and cloud settings. The few tools that intercept traffic (like Cloudflare) are optimized to avoid latency.
What about false positives?
This is common in security tools. Modern SECaaS platforms let you set thresholds and rules. You can fine-tune alerts so you’re only notified of what matters.
What happens if the SECaaS vendor goes down?
Most vendors offer uptime SLAs, backups, and redundant systems. But it’s smart to build a basic contingency plan, just like you would with your hosting provider or payment processor.
Quick Recap: What Should You Do Next
Here’s your 5-step starter plan if you’re considering Security-as-a-Service:
- Map out your current security gaps (start with identity, access, and data flows).
- Choose one SECaaS vendor that solves your biggest pain first (compliance, endpoint, etc).
- Test-drive it with a limited rollout or read-only mode.
- Build light automations or alerts and monitor behavior for a week or two.
- Expand usage and connect more tools as your confidence grows.
You don’t need a full-blown security team to start securing your business. You just need initiative and the right tools.
Why Security-as-a-Service Matters More Than Ever in 2025
Startups are moving fast. Markets are competitive. And customers are more privacy-aware than ever.
SECaaS isn’t just about avoiding breaches. It’s about building trust.
It helps you close sales.
It reduces the time to audit.
It protects your velocity.
It’s no longer an upgrade—it’s table stakes.
So, whether you’re an early-stage founder or a scaling VP of Engineering, don’t wait for something to break. Start secure, stay secure, and grow with confidence.
You might also be interested:


